121 | Add to Reading ListSource URL: www.aci.aeroLanguage: English |
|---|
122 | Add to Reading ListSource URL: www.armstrong.eduLanguage: English - Date: 2015-07-08 15:23:05
|
|---|
123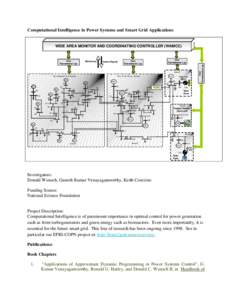 | Add to Reading ListSource URL: isc.mst.eduLanguage: English - Date: 2014-01-22 05:22:52
|
|---|
124 | Add to Reading ListSource URL: conferences2.sigcomm.orgLanguage: English - Date: 2015-12-02 16:47:09
|
|---|
125 | Add to Reading ListSource URL: www.winlab.rutgers.eduLanguage: English - Date: 2008-11-03 13:03:16
|
|---|
126 | Add to Reading ListSource URL: rlair.cs.ucr.eduLanguage: English - Date: 2011-01-19 19:25:19
|
|---|
127 | Add to Reading ListSource URL: www.winlab.rutgers.eduLanguage: English |
|---|
128 | Add to Reading ListSource URL: pds-geosciences.wustl.eduLanguage: English - Date: 2004-06-22 15:53:54
|
|---|
129 | Add to Reading ListSource URL: www.ijmetmr.comLanguage: English - Date: 2015-01-13 03:12:31
|
|---|
130 | Add to Reading ListSource URL: www.xiplink.comLanguage: English - Date: 2011-01-27 15:04:24
|
|---|